Ransomware attack escalating as Australian business hit

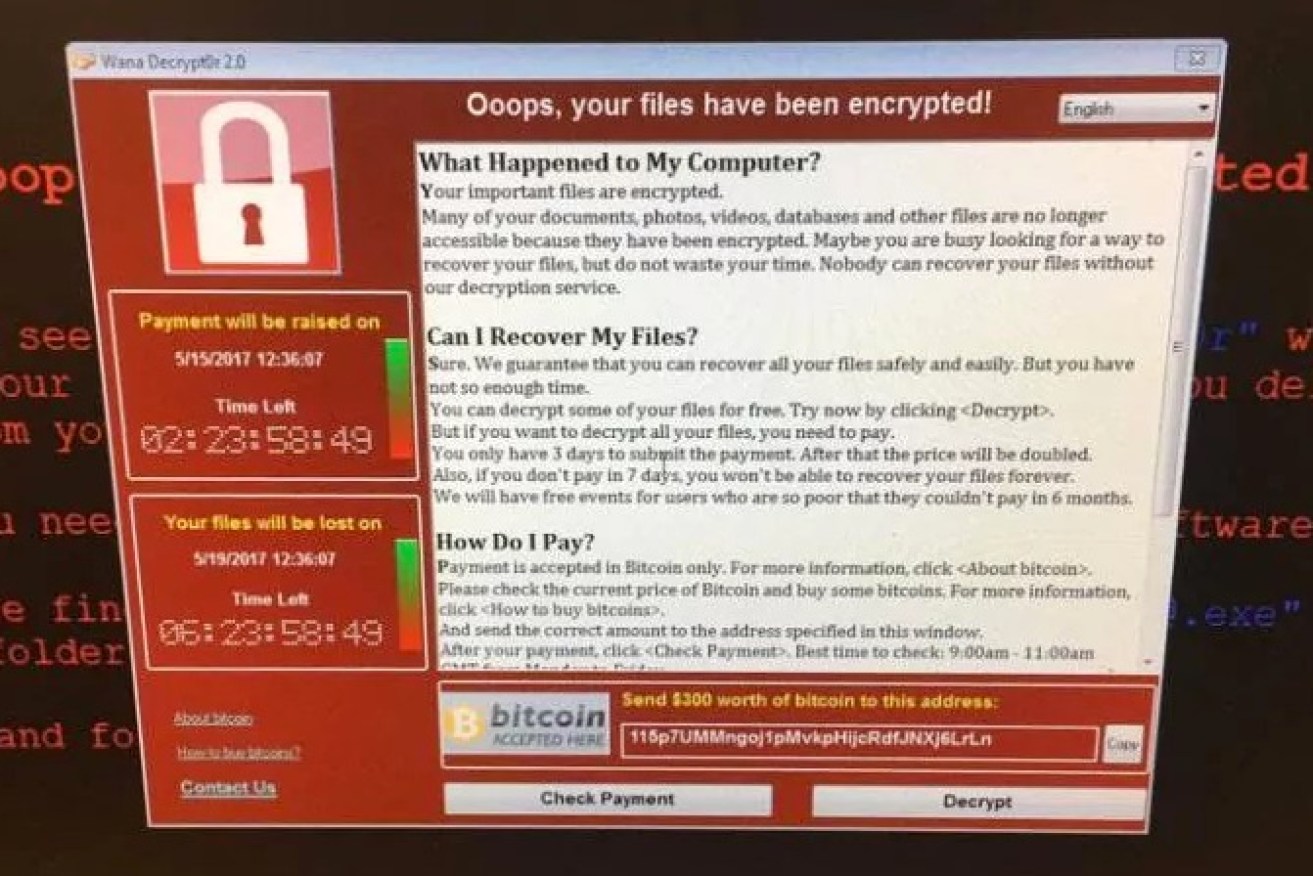
An Australian business has been hit by ransomware and there are reports of two others as agencies work to confirm links to the global attack.
The “unprecedented” global cyber-attack that wreaked havoc across Europe over the weekend has reached Australia, as cyber experts warn the worst may be yet to come from the ‘ransomware‘ virus.
Many workers, particularly in Australia and Asia, had logged off on Friday before the malicious software – thought to have been stolen from the United States government – began spreading across computer systems around the world.
As employees return to work and log on across the region Monday morning, the true effect of the attack may emerge, experts warn.
At least three Australian companies have been confirmed as being hit so far, but the federal government says more could find they have been compromised when staff turn on their computers Monday morning.
The cyber-attack, known as WannaCrypt or WannaCry, has so far affected more than 200,000 victims in 150 countries, according to Rob Wainwright, head of the European Union police agency Europol.
Mr Wainwright said the attack was “unprecedented in its scale” and warned many more people could find themselves affected.
“At the moment, we are in the face of an escalating threat,” he told British broadcaster ITV on Monday morning AEST.
“The numbers are going up. I am worried about how the numbers will continue to grow when people go to work and turn their machines on Monday morning.”
Russia and the UK were among the worst-hit countries by the virus, which took control of users’ files and demanding payments to release them.
The virus is already believed to be the biggest online extortion attack ever recorded, disrupting computers that run factories, banks, government agencies and transport systems in nations as diverse as Russia, Ukraine, Brazil, Spain, India and the US.
The Prime Minister’s cybersecurity adviser Alastair MacGibbon said critical infrastructure had not been damaged by the attack at this stage.
“We will see more victims here and that’s very sad always,” Mr MacGibbon told the ABC.
There are also fears that copycat variants of the malicious software have begun to spread.
“We are in the second wave,” Matthieu Suiche of United Arab Emirates-based cybersecurity company Comae Technologies said.
“As expected, the attackers have released new variants of the malware. We can surely expect more,” Mr Suiche said.
Australia’s Cyber Security Minister, Dan Tehan, says the government has received reports of the private sector being impacted, but not Commonwealth organisations.
“There has been one incident of the ransomware hitting a business here in Australia and there could be two other incidents where it has occurred, although we are trying to confirm that,” Mr Tehan told Sky News on Sunday evening.
“We’re not talking about a government organisation or a hospital or anything like that.
“We’re obviously working with that business, the Australian Cyber Security Centre is engaging with them.”
Mr Tehan said Australian business boardrooms needed to be conscious of the impacts of ransomware.
“And we’ve got to make sure at a departmental level, government level, departmental heads … that they’re taking the necessary steps,” he said.
“They’re aware of this. They became aware of it when we had the incident with the Census, so there are no excuses. They get well resourced for their information technology.”
In Perth, Senator Scott Ludlam warned Australians to keep their computers up to date against such threats and hit out against cyber-weapon creation by the US.
“We’ve seen what happens when the US NSA (National Security Agency) … develops hacking tools, effectively weapons for breaking in to ordinary people’s computers then loses control of one of those exploits that has then been effectively weaponised by a criminal organisation that is now seeking to ransom people,” he told reporters.
The ransomware attack struck the British government’s National Health Service, along with computer networks of companies and municipalities in dozens of other countries.
We apologise but we are having issues with our computer systems. Please don't attend A&E unless it's an emergency. Thanks for your patience
— NHS Blackpool Teaching Hospitals 💙🌈 (@BlackpoolHosp) May 12, 2017
A number of hospitals in England and Scotland were forced to cancel procedures after dozens of NHS systems were brought down in Friday’s attack.
Spanish telco giant Telefonica and US delivery service FedEx were among the businesses affected.
Attack could be reactivated with new code
The identity of the hacker who perpetrated the wave of attacks remains unknown.
Two security firms — Kaspersky Lab and Avast — said they identified the malicious software in more than 70 countries. Both said Russia was hit hardest.
“One thing that is very important to note is our sinkholing only stops this sample and there is nothing stopping them removing the domain check and trying again, so it’s incredibly important that any unpatched systems are patched as quickly as possible,” MalwareTech warned.
It also tweeted that while version one of the software was stoppable, the subsequent version “will likely remove the flaw”.
“You’re only safe if you patch ASAP.”
Security experts said it appeared to be caused by a self-replicating piece of software that enters companies when employees click on email attachments, then spreads quickly as employees share documents.
– With agencies








